SR&ED Documentation Best Practices To qualify for SR&ED tax credits, businesses must prove that they attempted to advance technology, faced challenges, and either achieved their desired outcome or didn’t. For this reason, documenting your progress or obstacles is extremely important to support your claim. To assist you during this critica
Read MoreStart Your SASE Journey with Cloud SWG
Start Your SASE Journey with Cloud SWG Superior, unified security. Exceptional user experience. Protect Web Traffic Without Slowing Down Your Business Here’s a quick, two-question quiz for you: Do you have a collection of security appliances in your server room that inspect all web traffic traversing your organization? Is your help desk fielding nu
Read MoreZero Trust Network Access For Dummies
Zero Trust Network Access For Dummies Ensure secure remote access for workers everywhere. The Next Era of Secure Access Is Here The work world has changed forever. Remote hybrid work and cloud computing are now unavoidable requirements to maintain user productivity and connectivity. Initial Zero Trust Network Access (ZTNA) 1.0 solutions may have h
Read MoreZTNA 2.0: The New Standard for Securing Access
ZTNA 2.0: The New Standard for Securing Access The past two years have dramatically changed all aspects of how and where we now work. Initiatives that were already underway, such as working remotely and cloud transformation, were suddenly and deliberately accelerated to accommodate our new realities. We now work in a world where work is […]
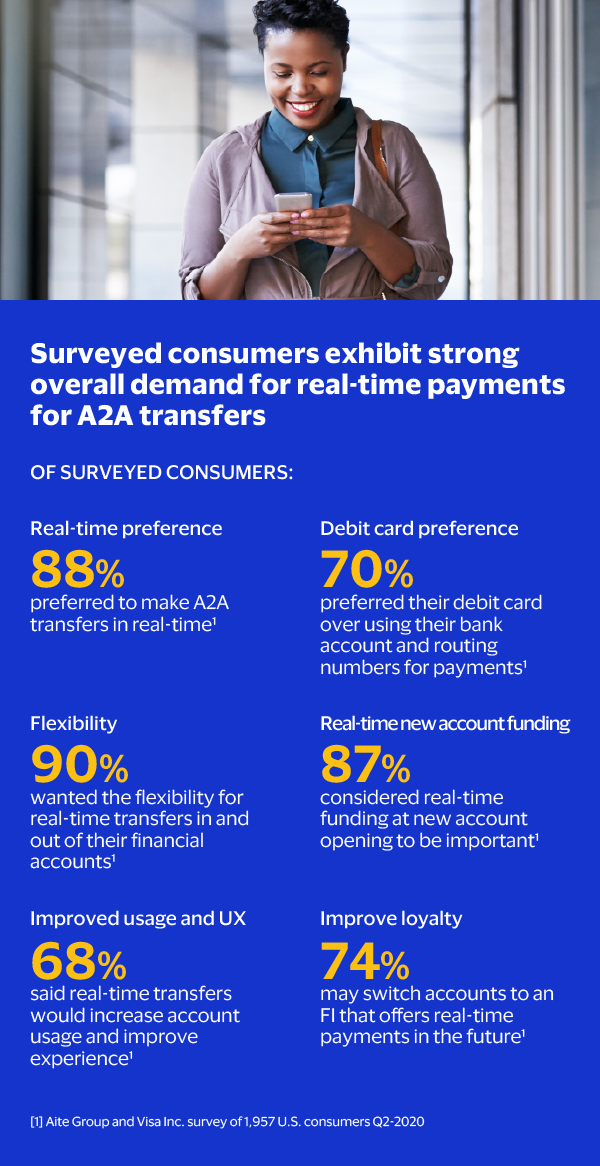
Read MoreCan banks and brokerages meet consumer demand for real-time1 transfers?
Can banks and brokerages meet consumer demand for real-time1 transfers? Download Visa Inc’s “Banking and Brokerage Consumer Study,” for insights into consumer interest for real-time1 money movement between their own financial accounts2 and the potential benefits for Financial Institutions and Brokerages. Visa commissioned research to understand beh
Read MoreGet Your SOC Ready for Zero Trust
Get Your SOC Ready for Zero Trust Effectively Monitor Zero Trust Access, Networks, and Endpoints In a world of digital transformation, a Zero Trust approach to security is critical for mitigating risk. The question is, how can organizations ensure that new policies are working as intended? It all comes down to your SOC—the place where […]
Read MoreSecurity Hygiene and Posture Management
Security Hygiene and Posture Management How leading IT and security professionals The growing complexity of attack surfaces has fundamentally changed the challenges of security posture management—and unknown risks only make it harder for your team to ensure security hygiene. How do market leaders accomplish this seemingly impossible task? This e-br
Read MoreProactive Security Operations from End-to-End
Proactive Security Operations from End-to-End Boost Your SecOps With the Cortex Portfolio With cyber threats rising by the hour, organizations need an end-to-end security solution that ensures that every step of their security processes and challenges are covered. This is where the Cortex portfolio shines, as you will discover in this informative b
Read MoreCreate an AI-Fueled SOC
Create an AI-Fueled SOC Learn How to Combat Advanced Threats and Improve SOC Effectiveness CISOs and security teams are under pressure to do more with less. They must keep up with constantly evolving threats using inadequate security technologies that cannot combat them. The good news is that this playbook will empower you with the insights needed
Read MoreHow Eight Organizations Transformed Their Security Operations with Cortex®
How Eight Organizations Transformed Their Security Operations with Cortex® Learn How Cortex Can Help Boost Your Cybersecurity The increasing volume of sophisticated threats seen on networks today is driving many companies to turn to solutions with AI—like Cortex®—to automate their cybersecurity. Read this eBook to get a better understanding of this
Read More