Axioms of Account-Based Growth Modern companies must adopt a strategic approach that treats individual accounts as markets to create long-term impact and support business priorities. Learn how to align marketing efforts, secure leadership buy-in, and develop a structured approach for account selection in this comprehensive whitepaper. While reading
Read MoreYou can have a zero trust model, but you can’t truly have zero trust
You can have a zero trust model, but you can’t truly have zero trust Who do you trust? With modern security, the answer should be almost no one. Zero trust can help prevent attackers from gaining access to key network assets. Yet applying zero trust principles to an extended network is extremely difficult, and doing […]
Read MoreWhat is your key to AI success? Trustworthy data
What is your key to AI success? Trustworthy data AI-powered analytics are improving business operations, driving innovation. and transforming customer experiences. Yet, they are only as good as the data that feeds them. Learn why it’s critical to ensure your data is accurate, complete, and secure. Key take-aways All AI models become stronger when
Read MoreThe Essential Guide to Observability for Cloud Native Environments
The Essential Guide to Observability for Cloud Native Environments Modern digital businesses increasingly rely on cloud native environments to deliver value to customers faster. However, while being cloud native helps a business scale, increase reliability and improve feature velocity, engineers have to tackle new challenges like increased complexi
Read MoreThe State of Observability 2023
RESEARCH The State of Observability 2023 Although observability is now ubiquitous, not all practices are created equal. In this global research report, we surveyed 1,750 observability managers, practitioners and experts and discovered the characteristics that set the most successful practices apart — as well as the massive payoffs they produce: Eig
Read MoreUnify Your Security Operations With Splunk
WHITEPAPER Unify Your Security Operations With Splunk In today’s cybersecurity landscape, security teams face challenges across people, processes and technology. Detection, investigation and response are fragmented between siloed tools, making it difficult to achieve intelligent situational awareness. Further, security operations center (SOC)
Read MoreA Beginner’s Guide to SOAR – How to Automate 5 Security Processes in Under 30 Minutes
ON-DEMAND A Beginner’s Guide to SOAR – How to Automate 5 Security Processes in Under 30 Minutes Let’s face it – manually performing repetitive security processes every day is boring. It creates fatigue and burnout for you and your team. What security tasks are you doing, day in and day out? Enriching URLs? IP reputation […]
Read MoreVR for Work Readiness Guide
VR for Work Readiness Guide VR for Work Readiness GuideVirtual reality is a technology that has the power to transform the way we do business. But you already know that. What you might not know is where to begin. In this essential guide to getting started, we’ll review Meta’s VR headsets and services, make sure […]
Read MoreA Strategic Framework For Enterprise VR Deployment
A Strategic Framework For Enterprise VR Deployment Virtual Reality Is Changing The Way We Work Recent research has suggested that the potential economic impact of the metaverse may add up to as much as $3 trillion in the next decade. But this fixation on the future misses a more important point. Extended reality (XR) technologies […]
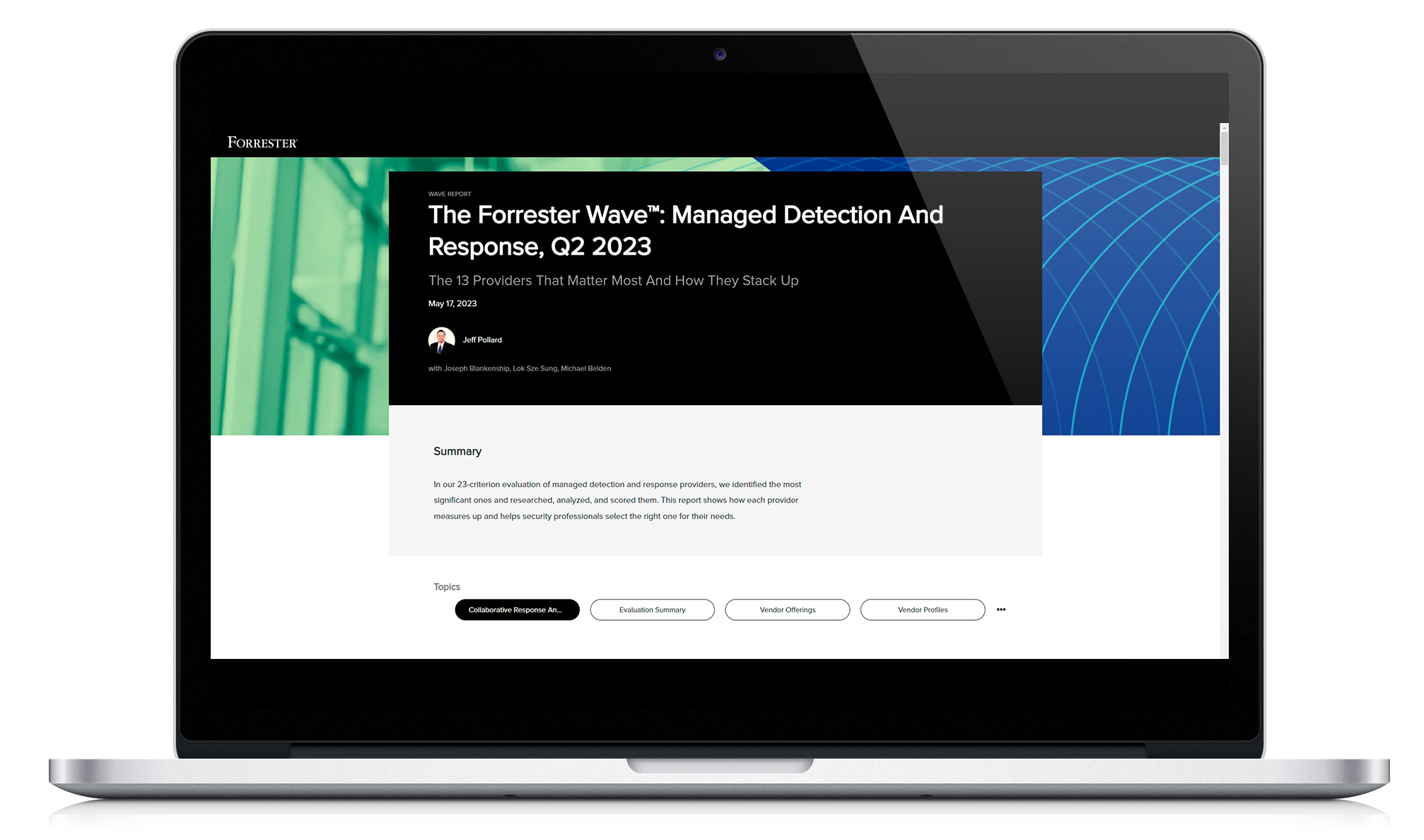
Read MoreThe Forrester Wave™: Managed Detection And Response, Q2 2023
The Forrester Wave™: Managed Detection And Response, Q2 2023 The Forrester Wave™: Managed Detection And Response, Q2 2023 is intended to help security teams find the right MDR provider for their needs. In this highly anticipated report, Forrester evaluates the most significant vendors to see how they stack up. Download the complimentary report to:
Read More