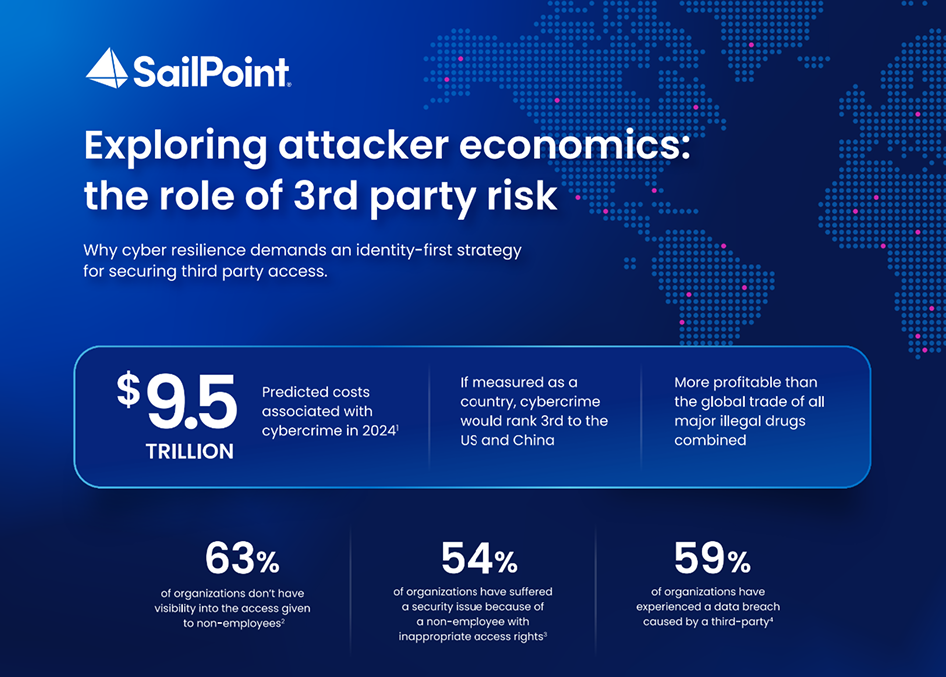
Non-employee access is risky business Research confirms prevalence of third-party breaches Approaching a data breach from the perspective of a cyber attacker provides insight into their motives, operational methods, and the economic factors driving their behavior. By understanding how attackers exploit vulnerabilities such as third-party identities
Read MoreSecuring the rise of machine identities
Securing the rise of machine identities How automation, AI, and bots are changing cybersecurity In today’s digital transformation era, machine identities have become cybercriminals’ favorite target due to their privileged access and lack of governance. Organizations are struggling to manage the proliferation of service accounts, bots, A
Read MoreWho’s Watching The Machines? An Effective Strategy for Managing Machine Identities
Who’s Watching The Machines? An Effective Strategy for Managing Machine Identities With machine identities now outnumbering human users, many enterprises and organizations face unprecedented risks from unmanaged service accounts, APIs, and automated processes accessing their critical systems. Without automated tracking, clear ownership, and proper
Read MoreMeet compliance every time with AI-driven Identity Security
Meet compliance every time with AI-driven Identity Security See how organizations are saving 4,300 compliance hours annually With global regulations constantly evolving and the average cost of non-compliance reaching $14.82M, organizations must transform their approach to compliance. Traditional manual processes are no longer sustainable, consuming
Read MoreSpecial Report: Horizons of Identity Security 2024‑2025
Special Report: Horizons of Identity Security 2024‑2025 Higher identity security maturity delivers outsized returns Cyber threats are evolving, and identity security is under increasing pressure to protect against growing attack surfaces while meeting the demand for seamless digital experiences – and showing a measurable return on investment. With
Read MoreBest Practices for Cloud Workload Resilience & Disaster Recovery
Best Practices for Cloud Workload Resilience & Disaster Recovery In this on-demand webinar, dive into the world of system resilience to learn popular techniques for recovering from a service disruption. In this session, you will explore how to craft robust cloud architectures, plus uncover AWS best practices for implementing resilience, includi
Read MoreA Guide to Privacy, Security & Risk Strategies for Generative AI
A Guide to Privacy, Security & Risk Strategies for Generative AI As the use of generative AI expands, it demands ongoing, meticulous attention. Effective privacy, security, and risk management are essential for safely scaling generative AI while meeting your organization’s governance requirements. In this on-demand webinar, you’ll l
Read MoreBlackbox.ai uses SambaNova Cloud to power agentic workflows
Blackbox.ai uses SambaNova Cloud to power agentic workflows Blackbox.ai is a leader in creating autonomous coding agents. With over 10 million monthly active users, they are trusted by Fortune 500 companies. The enterprise faced the challenge of meeting their clients’ growing performance demands and needed a powerful platform. SambaNova Clou
Read MoreDeepSeek R1 671B on SambaNova RDUS vs GPUs
DeepSeek R1 671B on SambaNova RDUS vs GPUs Today’s dynamic AI landscape requires powerful computing solutions that can handle advanced AI and ML workloads efficiently. To help companies keep pace, SambaNova Systems offers a groundbreaking platform that accelerates AI processing speeds. This video provides a demonstration, showing how Blackbox AI r
Read MoreZscaler Private Access Customers Realized 289% ROI
Zscaler Private Access Customers Realized 289% ROI VPNs were once the go-to for secure access, but they’re slow, expensive, and not built for zero trust. That means more security gaps, frustrated users, and mounting IT costs. So how do you know if your remote access solution is truly secure? This Total Economic Impact™ report breaks it down—showing
Read More